Imagine if, one day, all commercial banks eliminate the process of signing checks and other bank documents for transactions. It would wreak havoc across the banking system.
Why is it so?
A decision as small as this will create a lapse in authenticating the identities of millions of account holders. It will make it possible for people to forge identities, leading to massive security breaches.
This was a very basic example of why identity governance and administration are needed in the realm of cybersecurity.
We live in the age of digitization. As more and more organizations expand their IT environments, the need for identity governance and administration increases. More people lead to more identities that need seamless management. Companies cannot afford to compromise the security of their assets by giving wrong access to the incorrect individuals.
This is where identity governance and administration comes to your rescue.
What Is Identity Governance And Administration?
Identity governance and administration (IGA) is the area of cybersecurity that lets security administrators manage user identities across an organization. It tackles both cloud-based/remote and on-premise systems. IGA improves your visibility into the identities of your employees and their access privileges.
This helps you implement better control to prevent risks associated with inappropriate access. Simply put, IGA is all about preventing employees from receiving excessive or incorrect access across the digital environment.
In the digital age, access control remains the most important domain in cybersecurity. A recent study by Verizon shows that 63% of confirmed data breaches occur due to weak, stolen, or default passwords. Companies cannot afford to lose their digital gold (data) because of such issues. With identity governance and administration, they can automate their employees’ access to IT assets without compromising security.
Key Features Of Identity Governance And Administration
IGA lets you streamline user identity lifecycle management by provisioning and de-provisioning user access. To understand the IGA features, we need to know the components related to identity governance and identity administration.
Let us start with the IGA components related to identity governance:
- Segregation of Duties
Segregation of duties (SoD) involves the creation of specific rules that prevent the allocation of risky access or transaction rights to a single user. Continuing the banking example used earlier, an organization may create an SoD control to prevent a single user from viewing a corporate bank account and making fund transfers. This ensures that the funds in the concerned corporate accounts are secure.
- Access Review
Access review involves viewing and analyzing user access across multiple resources and applications. Continuous access review ensures an updated ecosystem, simplifying processes like access revocation when an employee leaves the company.
- Role-based Access Management
As the name suggests, role-based access management involves assigning access to an individual according to their role in the organization. It ensures that an employee receives access limited to the duties they are expected to perform.
- Analytics And Reporting
Continuous analytics and reporting allow the cybersecurity team to raise alarms during risky situations, address policy violations, and create detailed compliance reports. They also allow the security personnel in an organization to suggest necessary changes to the rules and policies involved.
Let us now dive into the IGA features related to identity administration:
- Integrations Connectors
Integration connectors allow your IGA solution to integrate with all enterprise systems that contain information about different users and the systems they have access to. They perform the valuable function of reading this data to understand which user has access to which resource. The connectors also write data to create new user identities and give them appropriate access.
- Automated Access Request Management Workflows
These workflows automate the process of requesting access to specific systems users need to perform their tasks. They also help admins onboard/offboard users, determine role-based access, and approve user access.
- Provisioning
An IGA solution facilitates automated provisioning and de-provisioning of access at both user and application levels. Security personnel can use this for both on-premise and cloud-based resources.
- Entitlement Management
Entitlement management lets your security personnel verify what different users are allowed to do in different applications or systems.
What Are The Benefits Of Identity Governance And Administration In 2024?
While rapid digitization has made all our lives easier, it has come with its own bunch of cybersecurity challenges. Before moving on to the benefits of IGA, here are a few challenges it helps us resolve:
- Manual user administration for a big team
- Longer onboarding times
- A lack of automation
- Access management complexity
- Risky compliance and regulatory requirements
- Risk of subtle data breaches
- A lack of visibility and control
Let us now understand the major benefits of identity governance and administration:
- Streamlined User Identity Lifecycle Management
From the moment a user is onboarded to an organization until they leave, they pass through multiple stages. Managing this user identity lifecycle is an extremely complex process, especially in large-scale enterprises. From provisioning to de-provisioning, IGA helps you automate a number of processes, making such management simpler and faster.
With IGA, your security personnel need not worry about maintaining manual control over your users, devices, networks, and all relevant IT resources within your organization.
- Tracking Risky Access Requests
Granting risky access may have long-term implications for an organization. IGA gives you a centralized approval location where all users can request access as per their requirements. All these requests are analyzed and granted only if they are risk-free.
- Improved Security And Compliance
Especially through detailed reports and analytics, IGA solutions help admins get a better idea about the goings-on throughout their enterprise environments. This helps them identify, analyze, the mitigate risks in no time. Moreover, data centralization makes it possible for admins to audit multiple access reports and meet compliance requirements.
- Improved User Productivity
IGA not only benefits your security personnel but also users working on multiple systems and applications. Whether they work on-premise or remotely, it gives your employees the much-needed flexibility to work freely without waiting too long for genuine approvals.
- Better Scalability
With automated workflows and centralized policies, robust IGA solutions help you reduce operational costs and ensure that all users receive the access they need without any hindrances or delays. Such processes have a direct impact on an organization’s scalability.
Typical Use Cases Of IGA Solutions
An IGA solution has a number of use cases that help an organization build a rock-solid IT infrastructure. Here are the most common use cases of the same:
- Creating a user and managing their system access through provisioning for a joiner
- Taking away system access rights and ending a user’s lifecycle through de-provisioning
- Adding or removing user access for specific systems/applications and transferring the same for a new role if an employee moves to a different position
- Re-assigning roles and managing user access for employees re-hired by an organization
- Monitoring orphan accounts
- Facilitating single sign-on in the case of cloud services
- Facilitating adaptive authentication
- Managing passwords for all users and facilitating automated changes/updates for the same
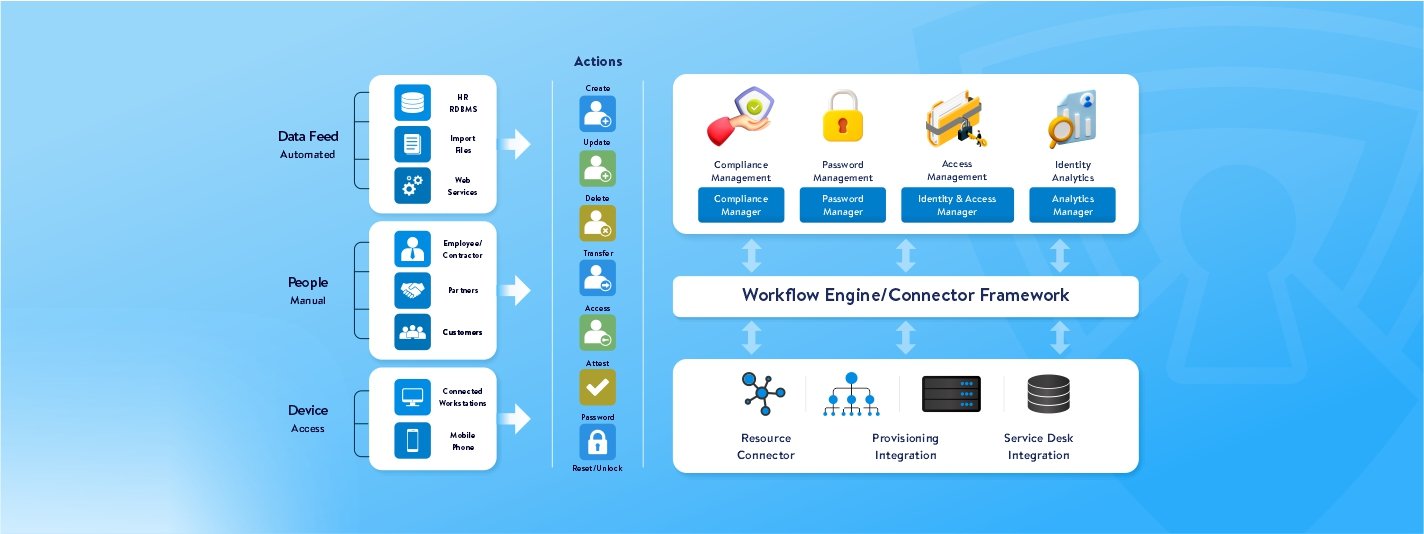
Typical IGA Deployment Architecture
To understand the deployment architecture of an identity governance and administration solution, it is important to focus on two key aspects – types of deployment and typical IGA components.
Let us start by understanding the two major IGA deployment types:
- On-premise IGA Solution
An on-premise IGA solution involves a deployment model where the software and its infrastructure are installed and operated within your company’s data center or on-site server. Here, your organization will have full control over the software, hardware, and data associated with the concerned IGA solution. Such a deployment model is preferred for organizations with strict regulatory compliance obligations.
- Cloud-based (SaaS) IGA Solution
In this deployment model, an IGA solution is hosted as a SaaS (Software-as-a-Service) solution by a specific vendor. It works on both on-premise and cloud-based applications. This is the perfect deployment model for companies working on a hybrid model, catering to employees working both on-premise and remotely.
Now that we know the key deployment models, let us have a look at the key components of an IGA solution:
- Users/Identities– The employees working in an organization
- Application Accounts– Accounts created specifically to interact with specific applications within a company’s IT environment
- Workflows– Pre-defined sequences of tasks that automate a number of identity governance and administration processes
- Forms– User interfaces that collect and showcase valuable information related to identity management processes
- Rules– Pre-defined conditions or criteria that automate specific processes, enforce access controls on users and govern identity-related procedures
- Policies– The rules, guidelines, and principles determine how different user identities are managed and access rights are granted/revoked. Common examples include access control policies, password management policies, data retention policies, segregation of duties, etc.
- Application Connectors– The software components facilitating integration between your IGA solution and external applications
- Roles– Access rights given to users based on their job duties and responsibilities
- Entitlements– Access rights are given to users that determine the actions they are authorized to perform on specific applications or systems. They are more granular than roles.
- Reports– Structured and detailed summaries related to compliance metrics, user identity-related data, audit trails, and more.
- Email Templates– Pre-designed layouts to send emails to different users, admins, and other stakeholders throughout the identity governance and administration process.
- Identity Analytics– The process of using modern data analytics and technologies like machine learning to obtain valuable insights from your identity-related data and a user’s identity life cycle.
Major IGA Product Vendors
Multiple vendors across the globe offer robust identity governance and administration solutions to their clients. Let us have a look at some of the most prominent players:
- SailPoint
One of the most popular IGA solution providers, SailPoint (or SailPoint IdentityIQ) empowers your cybersecurity personnel by giving the right employees access to the right applications at the right time. Along with creating role-based access for new users, SailPoint helps you discover and extract insights from the SaaS applications used by your organization.
- Saviynt Identity Cloud
A product of Saviynt, a leading cloud-native identity management solution provider, Saviynt Identity Cloud is an IGA solution that helps organizations of all scales manage and secure user identities across the board. It helps you access rights and data across on-premise, cloud, and hybrid environments.
- Microsoft Entra ID
Formerly known as Azure Active Directory, Microsoft Entra ID is a popular IGA solution by the software giant. It is a cloud-based identity and access management tool that helps you connect employees, customers, and partners to their respective devices, data, and applications. It is best known for its quick and seamless sign-in experience across multi-cloud environments.
- Oracle Identity Manager
Oracle Identity Manager helps your cybersecurity team manage all your users’ identity lifecycles with high precision. It also provides impeccable security to both cloud-based and on-premise applications your company uses. Oracle Identity Manager, you can ensure that timely reports are sent to your IT units to keep everyone on the same page.
- ForgeRock Identity Management
ForgeRock Identity Management gives you a simple yet comprehensive IGA solution. The single and unified platform excels in identity management, access management, directory services, user-managed access, and identity gateway services.
- One Identity
One Identity empowers your IT team to grant users secure access to all your applications, systems, and resources while being in sync with the action policies. It also provides identity governance as a solution to help your IT team automate provisioning, de-provisioning, and access requests. Its biggest strength lies in giving you a unified platform equipped for IGA, identity security, privilege access management, and much more.
The Final Word
After going through all this information related to identity governance and administration, it is safe to say that we have barely scratched the surface! IGA is an elaborate but incredibly rewarding section of cybersecurity that helps you build a rock-solid IT infrastructure. Implementing the right IGA solution will not only make your security personnel’s work easier but also make your employees more productive, giving your business the scale it deserves. It is no less than giving your IT team a protective shield as you build your cybersecurity empire!